Our secure technology
The delivery of secure IoT end-to-end is the key common feature across AddSecure’s solutions.
Secure IoT solutions end-to-end
By enabling data to be transmitted securely through our IoT connectivity platforms, for the provision of software-enabled services, we can offer differentiated end-to-end solutions tailored to meet the needs of customers in various industries. The delivery of secure IoT end-to-end is the key common feature across AddSecure’s solutions.
About the technology
Our secure IoT solutions have a common technical architecture model, managing events from a connected device that transfers data through a secure connection to a software application that in turn provides information or notifications to the recipient, such as an Alarm Receiving Center (ARC), which can respond to the event.
The secure and reliable end-to-end solutions are generally built on three different components: hardware (with integrated software), secure communications and data management, and software-enabled services.
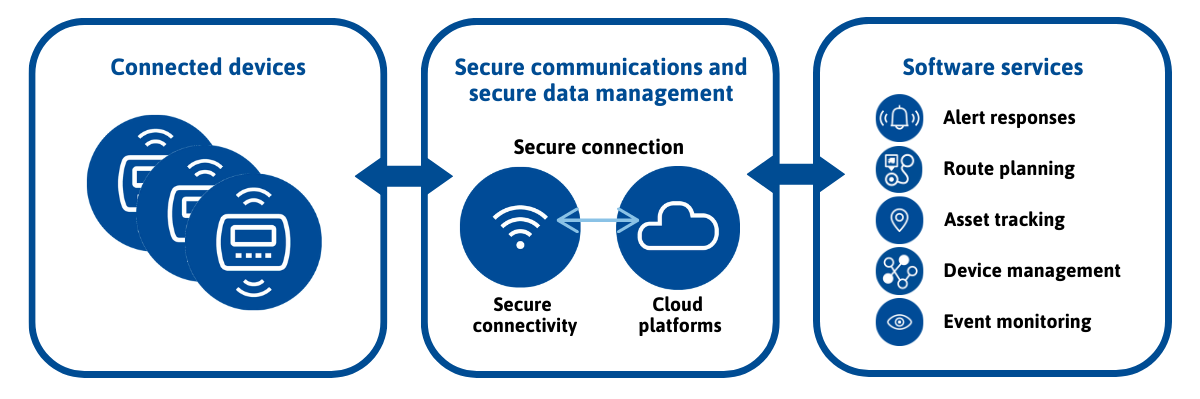
We either procure the hardware from third-party providers or develop our own in order to offer our differentiated IoT end-to-end solutions.
The data or signals from the connected devices are transferred through a secure connection either wirelessly or through a fixed line. The wireless secure connectivity is delivered via telecommunication networks, which we offer to our customers packaged with our solutions.
In addition to providing the secure IoT connectivity for our customers, we ensure that the data transferred from the device to the recipient is completely secure. Our IoT solutions provide end-to-end security through a private cloud (VPN), routed through our back-end infrastructure and data centers, ensuring that the signals or data arrives to the correct recipient without any data leakage or interception.
How we define secure communications and data
We define secure communications as in two or more devices communicating information that is truly critical to either a business’ operation, to people’s lives, or to vital societal functions. To us, secure communications means that this connection between the devices is reliable, accessible and that it cannot be intercepted or interfered with.
Data is the information itself. To us, secure data means that this information not only get from point A to point B without interception or interference, but also that it is reliable, only available to authorized parties, and that it is stored and used in an ethical manner with regards to privacy.

Why secure communications and data is so important
Getting data from point A to point B in a secure way helps save lives, protect property, and secure vital societal functions. Learn more in this video!